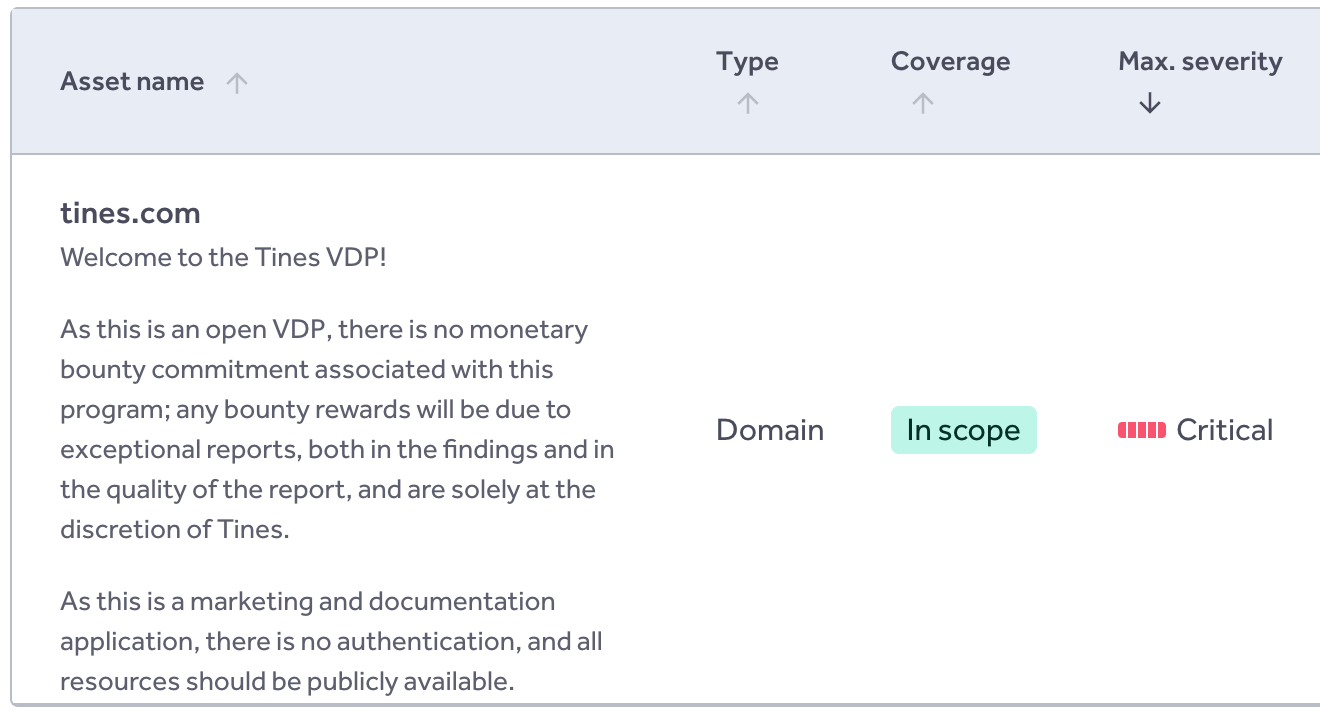
For this exercise, I reviewed the scope of a public HackerOne VDP to understand what was allowed.
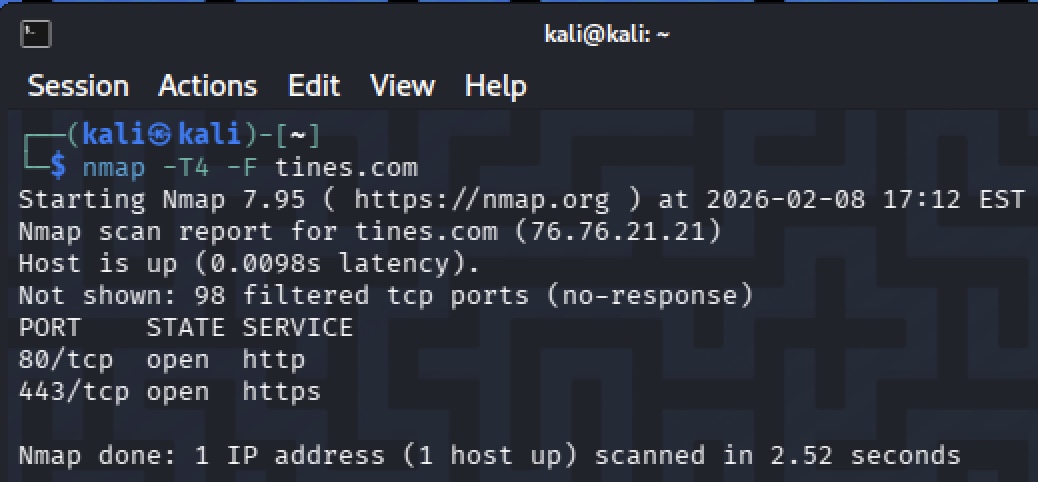
After that, I did basic non-intrusive reconnaissance on an approved domain.
I used concepts I learned in GSEC and GCIH. The goal was to validate scope, see what assets were exposed, and practice safe reconnaissance without crossing any boundaries.